|
BIM 1.0
|
|
|
BIM version 1.00 is a free Java based AOL instant messenger client Authors: Contributors:
Links: Table of Contents
What does it do? BIM is a Java based AOL Instant Messenger Client with encryption support. It has a small code base (617KB w/encryption libs) and can be easily run on wide array of operating systems. BIM has been tested on OSX, Windows XP, Solaris and Linux. In addition to standard instant messaging capabilities BIM also incorporates encryption technology so that a user can communicate securely with any other BIM user. Why is this cool? (The encryption that is) I think pictures speak louder then words so I decided a demonstration was in order. Using another brilliant open source product, PlugProxy, I was able to take a quick screen shot of what goes over a TCP connection when connected to AIM. As you can see the connection is not secure at all, everything is sent as clear text. A user is vulnerable to both eavesdropping and message alteration. 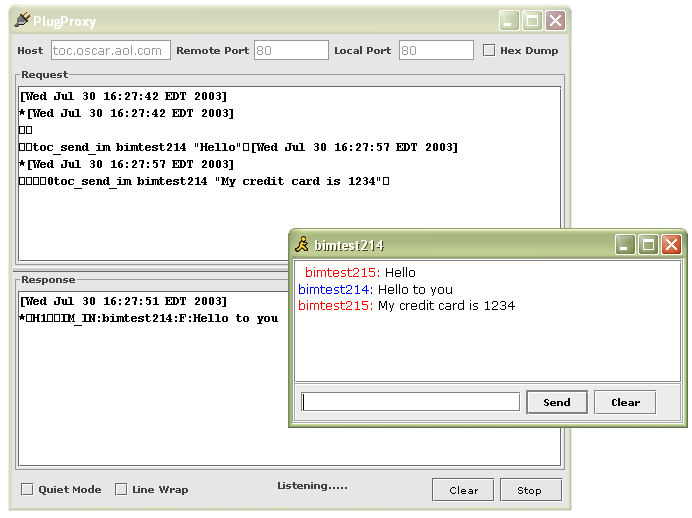 In addition to your messages being compromised, you have no way of knowing for sure that your buddy's messages are genuine. They could have their connection altered much in the same way as your could be. A true security solution encompasses the following:
BIM addresses all three of these issues. BIM can run a chat session in what is referred to as secure mode, although BIM's secure messaging involves more then just encryption. Unlike other IM clients, BIM actually addresses all three of these issues. Every unique user of BIM can generate a public/private key pair for security use. BIM's security hinges on the secrecy of this private key, BIM will never send this key over the network however it is up to the user to secure the key on their local machine. Private Messages BIM does use encryption in order to send messages safely to other users. BIM uses RSA encryption to ensure only the intended receiver can decrypt your message. It does this by encoding each message with the public key of the recipient. By doing so only the intended recipient (and the NSA perhaps :)) can properly and easily decrypt each message. Authenticated Messages BIM uses digital signatures for the verification of messages. To be more specific BIM creates an MD5 hash of each message, which is then encoded using RSA again as specified by PKCS#1. This signature for each messages is appended to the message and serves two purposes. It allows the recipient to verify it was in fact the send of the message who reated this message, more specifically it proves the message was not sent by an imposter. In addition the signature verifies the content of the message, namely that the message was not altered in transit by a third party. Verified Messages All transactions in BIM (and most PKI schemas in general) begin with two parties swapping public keys. In order to prevent the famous man in the middle attack, public keys are signed by a certificate authority. Users can then verify the identity of the user sending them the public key. BIM does address this and comes with a bot (CAbot) which runs on the AOL network and can give out certificates. CA-bot in its current state is not that useful though for the following reasons:
java -cp bim.jar wellington_brad.bim.cabot.CaBot You should see aol id cabot215 come online. When BIM is running in secure mode, it becomes very difficult for a potential attacker to do anything but prevent communication. Here is picture of the same AOL conversation using PlugProxy as was shown above, this time in secure mode. Here is a link to a presentation I did on some of these issues. 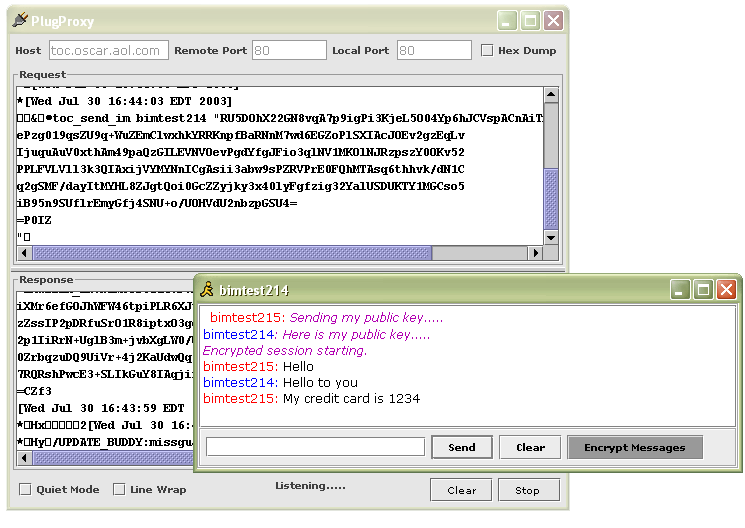 What do I need to run BIM BIM's sole requirement is that you have JDK 1.3 or above on your machine. You can download the latest version of Java from Sun's website. How do I use it? The directions for BIM are broken into several sections.
Option 1: Run BIM via webstart here if you have webstart installed. (All jdk 1.4+ installations install it by default) Option 2: After downloading the BIM jar file, simply run it with the jar command in Java. Many Operating Systems will even allow you to double-click the jar file. java -jar bim.jar After BIM starts the login dialog will appear. It looks like this: 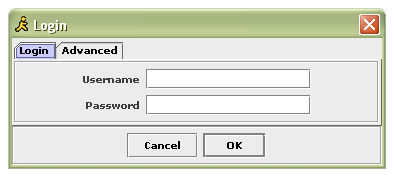 Simply type in your username and password and you should be all set. The advanced tab has options which allow you to specify which AOL server you wish to connect to, and also allows you to change the port. This is especially helpful in environments where you wish to use AIM but cannot due to closed ports (ie. a firewall) The Buddy ListThe buddy list is very similar to every buddy list. It contains a list of your contacts sorted by group, it also has shows which of your buddies has been idle and for how long. 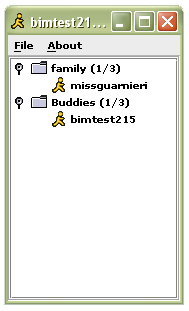   To start a chat with a buddy, simply double click on that buddy's name and a chat window will open.
The chat window is used to converse with a particular buddy. A chat window can be launched from the buddy list, or one will appear when a user is contacted by someone else.  Messages sent by you will appear with your name in red. Messages sent by your buddy will appear with their name in blue. Auto-generated messages will appear in purple. To send a message simply type your desired message in the test field at the bottom of the screen and press the send button. To clear the current conversation from the screen use the clear button. User PreferencesThere are three primary function points for the User Preferences dialog. General Information TabThe first tab is meant for the saving of login information. If this information is changed it will not be accessed agin until the application is restarted, and it will not be saved automatically. The user must hit the save locally menu item located on the buddy list file menu.  Buddy List Editor Tab The second item that can be adjusted from the preferences dialog is structure f the user's buddy list. Here users can add buddies, add and remove groups and re-order their existing list using drag and drop. Please note that while the buddy list will be altered for the remainder of the session, it will not remain altered. In order to permanently save a changed buddy list a user must select the Save to Server from the file menu on the Buddy List screen.  Encryption Manager Tab The final item that can be controlled from the user preferences dialog is the encryption functionality. This is the screen a user goes to in order to enable encryption as well as manage keys.  Using Encryption The first thing to do in order to enable encryption is to generate a keypair. This can be done from the encryption manager tab, as shown above. Once this is done the enable encryption checkbox on the encryption manager becomes available. Check this and encryption will be enabled. The next thing to do is bring up a window with your buddy's name (note this buddy must also be running BIM with encryption enabled for this to work). You will notice that there is now a third button on the chat window. Pressing this button will initiate the encrypted chat. This will only work if you buddy is using BIM and they have encryption enabled!  If your buddy has not gotten a signed key from the CA, it will give you a warning that you are dealing with an unsigned key. Encryption is now enabled and you may chat knowing no one is listening in. You may switch back and forth from clear text mode by pressing the toggle button. How does this work? Java Java will be used as the language to implement BIM. Bim will be compatible with JDK 1.3 and above. Swing will be used to build the user interface, and the Java Cryptography Architecture will be used for encryption and message signing. The application will be platform independent. BIM's GUI was built using an MVC client architecture. the javadoc can be found here. AOL's hidden proprietary network protocol is called Oscar. TOC is an open-source project that allows any client to interface with AOL's central server. Cryptix is an open source implementation of the Java Cryptography extension. It contains an RSA cipher, RSA Key Generator and an RSA Signature algorithm. These three core classes which will be used in conjunction with Sun's JCA (Java Cryptography Architecture) to generate the needed security requirements. For encryption BIM uses RSA with a 1024 bit key, and it uses an RSA MD5 digest for the signatures. Please note again that there is little to no local protection for private keys. If your machine is compromised, so is your secure communication. BIM never sends any private key information out over the network though so you may feel fairly confident that is your machine is safe, so are your messages. Enjoy! I hope you find BIM useful. |